I think it is important we get something clear from the start – Zero Trust is not a technology; it is not a system. Zero Trust is a concept, an approach, a strategy. An identity platform is not a Zero Trust solution, it is part of a Zero Trust infrastructure – a critical part, but still a part.
What is interesting to me is how the various component parts that underpin a Zero Trust based infrastructure can be viewed at the micro level or the macro level. And when we step up to the macro level, how the wider benefits of the architectural components can also deliver top and bottom-line benefits beyond the delivery of a controlled perimeter around a defined protected resource.
Components of a Zero Trust architecture
The most fundamental aspect of Zero Trust is determining what you want to protect, i.e. defining the protected resource. Once this is understood it is then possible to start looking at the strategies for protection.
Detailed definitions of the components of Zero Trust of course vary. However, there are a few core components that are common to (almost) all.
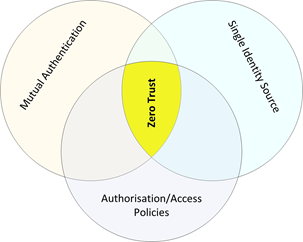
- Mutual authentication – who is accessing what
- Single identity source – the definition of ‘who’ and ‘what’
- Authorisation and access policies – the allowed operations/activities for ‘who’ interacting with ‘what’
Intersect these components and you have the basis of a Zero Trust approach.
The role of Identity
Looking at the common components above, this feels familiar. Those three items are also components of any Identity and Access Management (IAM) platform.
A single source of identity is important. This doesn’t preclude building on external identities by using, for example, federation, but having a closely coupled ‘Zero Trust’ protected identity source is critical to ensuring accuracy and control of the identities in use.
The identity needs to be assured and well authenticated. The actual level of assurance will be defined by the analysis of the needs of the protected resource, but it is important to know to a defined level how sure we are that the presented identity is ‘who they say they are’.
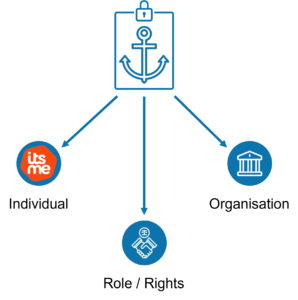
Further, the identity needs to include all necessary information. This is not referring to ‘thin file’ considerations, although that should always be a consideration, but to the nature of the identified entity. Not only individuals interact in transactions, organisations do as well. In fact, the majority of transactions involve organisations as at least one of the parties. The identity system must be able to support organisation identity as a primary identity class or you will always have an ‘indirection’ in place, and that is an attack vector.
Access management, through access policies and authorisation, is by definition at the heart of any Access Management platform. Having a minimal set of policies to define access to the protected resource is a core part of a Zero Trust solution. Moreover, these policies need to be tracked as close to real time as possible to ensure the latest information is always available.
The bigger picture
 If we take the principles already discussed and then move up to a higher-level view, we open up the possibility of business level benefits beyond ‘security’.
If we take the principles already discussed and then move up to a higher-level view, we open up the possibility of business level benefits beyond ‘security’.
Having an identity platform that anchors individuals and organisations, coupled with near real time access control information, enables entities to participate dynamically in transactions with appropriate authorisations.
If we add in a delegation capability – see the Ubisecure Identity Platform’s advanced Identity Relationship Management – then we have the basis of a representation governance platform, built on the components already in place for a Zero Trust based deployment.
We’ve discussed the value of representation governance previously. The ability to move governance from administrative controls to technical controls brings proven top- and bottom-line benefits to organisations.
If you would like to see a case study that shows a 99% saving based on these techniques, or to see how you could generate business value from your Zero Trust strategies, then please get in touch.



About The Author: Simon Wood
As Group CEO at Ubisecure, Simon is responsible for planning, communicating and delivering Ubisecure’s overall vision and corporate strategy to enable the true potential of digital business through modern identity management solutions.
More posts by Simon Wood