2020 has seen remote working become the new norm, with many predicting that remote working will continue to prevail beyond the pandemic.
With this in mind, many businesses have had to raise urgent logistical questions around employees staying connected and maintaining access to internal systems efficiently and securely. Naturally, digital identity plays the central role in organising access to business applications, regardless of user location (in the office or remote).
Verifying user identities and managing appropriate access to various resources is a key aspect of both internally (employee) and externally (customer) focused applications. However, until now, the management of these internal and external identities has been treated differently by organisations. In this article, I’m exploring why that’s now changing, and how it affects you.
IAM vs CIAM: until now
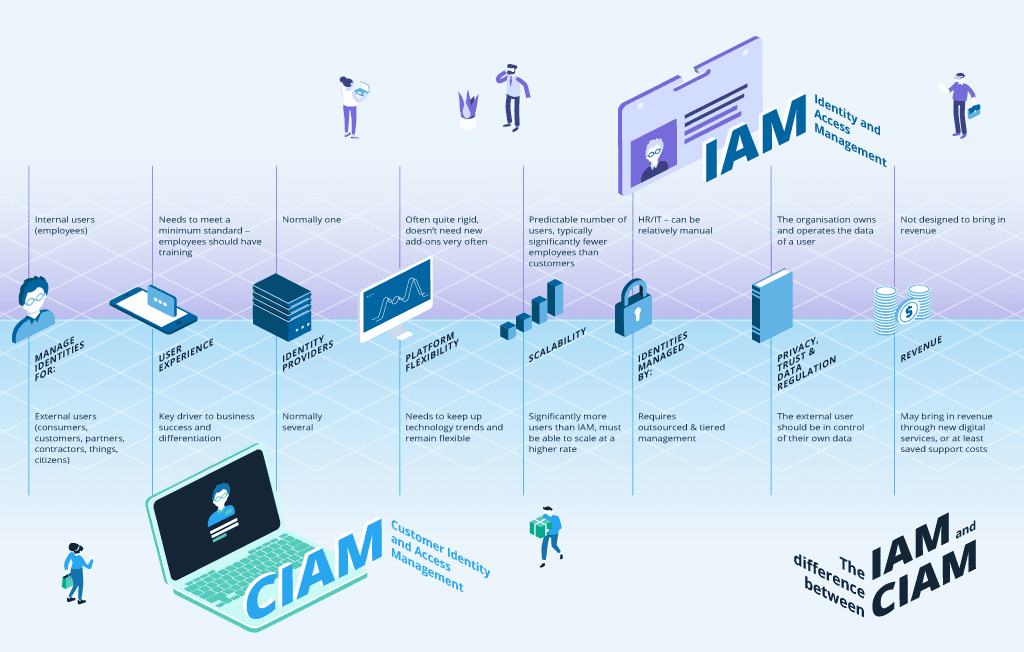
Many businesses have faced the pitfalls of attempting to make employee IAM – aka traditional/legacy/enterprise/internal IAM, built for in-office, workforce identities – work for external users (customers, partners, citizens etc.).
The assumption that ‘one IAM fits all’ has left businesses unable to cope with external user demands for usability and scalability, alongside different necessary approaches to regulation adherence.
These issues saw the emergence of Customer IAM – a subset of IAM that is specifically designed for external identities. For example:
- Greater focus on seamless user experience, e.g. with various options for authentication
- Putting users in charge of their own data and account access delegation, to support scalability
- Regular platform updates in line with technology trends, rather than a fixed system
Enlarge infographic (opens in new tab)
IAM and CIAM in 2020: new ‘blurred lines’
When it comes to remote working, however, the typical internal user starts to look and behave a lot like an external user, increasing the importance of CIAM-specific capabilities. The lines between IAM and CIAM have started to blur.
Employee IAM is traditionally something that new starters are trained to use face to face. Any nuances of the system become familiar over time, with the ability to ask colleagues sat nearby for assistance when needed. In contrast, Customer IAM removes any user experiences obstacles for external users, who don’t have training or the patience for clunky identity workflows. Similarly, remote workers will not be able to receive face to face training – a scenario that would be better served by the accessibility of CIAM.
Many employees may now be recruited and onboarded without ever meeting their colleagues in person, which throws up needs that are better met by CIAM – for example, remote identity verification with international identities as opposed to a manual process with HR.
Further, while every interaction now needs to be digital, hacking and phishing incidents are on the rise. This means that secure access, to only the right resources, from any location, is more important than ever. Again, something that’s facilitated by CIAM’s ease of use – think identity providers (IdPs), delegated authority, risk-based authentication (RBA) and options for multi-factor authentication (MFA).
Let’s take RBA as an example. In an office environment, staff are typically asked for a password in order to gain access to applications. The location of the device, the browser, the time of day etc. are unlikely to change. If a hacker is sat at an employee’s desk trying to gain access to the systems, other staff members will notice. However, in a remote situation, the employee’s device IP address, the time zone, the device itself, may all be unpredictable. In this case, RBA workflows would recognise where additional, stronger authentication factors are needed, until the device and other situational factors are authorised and trusted.
To take the earlier incorrect assumption that ‘one IAM fits all’, the shift to remote working has shown us that, in fact, ‘one CIAM fits all’.
What does this mean for organisations?
If your employees have been asked to work from home this year, you’ll already know if your internal systems have stood up to the challenge of remote identity and access management.
If they have, operational efficiency will not have changed since employees were office-based. For example, there will be no increase in IT Support having to sort out login issues, or employees wasting time trying to gain access to necessary services.
If not, this article may explain why. For these businesses, you’ll need to implement a solution to help you deal with these now-external identities – fast. Try Identity-as-a-Service (IDaaS).



About The Author: Francesca Hobson
As Senior Marketing Manager, Francesca aims to provide valuable insights on digital identity through our Let's Talk About Digital Identity podcast, blogs, industry events and content library.
More posts by Francesca Hobson